Over the years, hackers have stolen millions of dollars worth of digital currency from multiple exchanges. The digital currency market attracts a large number of talents. Investors and others want the highest return and will not be influenced by anyone.
Once your digital currency is stolen, you will not be able to get a refund, and transactions and assets will not receive any protection, which makes investing in digital currency really dangerous. A large number of digital currency transactions cover a large amount of digital cash. These factual factors are very attractive to hackers.
In the past 8 years, about 31 digital currency exchanges have been hacked, and some exchanges have been stolen many times. More than 1 billion U.S. dollars in digital currency (actually 1.3 billion U.S. dollars) was stolen. Some digital currency exchanges learned from it and managed to recover their losses. Most other exchanges that were stolen went bankrupt. Like Mt.Gox, Bitcoinica, PicoStocks, Bitcurex, they have even been attacked many times by hackers.
Today, more than 200 digital currency exchanges provide their services to customers, and this number is constantly changing. Therefore, a decline in the digital currency of an exchange or a hacker attack will not cause a decline in trading volume. The market, just like before, many countries have begun to do this, introducing regulatory requirements for digital currency exchanges, but still not all investors can be fully protected and lose their assets. Therefore, we should learn from experience, invest in reliable assets, diversify your portfolio and choose a good digital currency exchange.
In preparing this security rating, we have evaluated the security measures and the following potential vulnerabilities that may have a negative impact on the exchange and its users.
The report will discuss the following issues in detail:
• Console error
• User account security
• Registrar and domain security
• Web protocol security
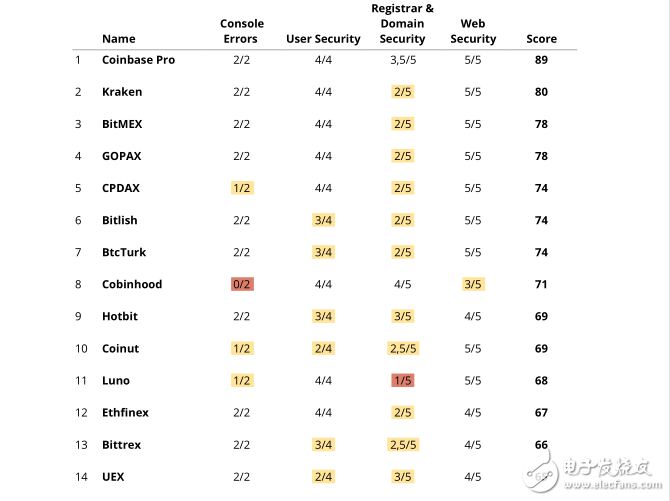
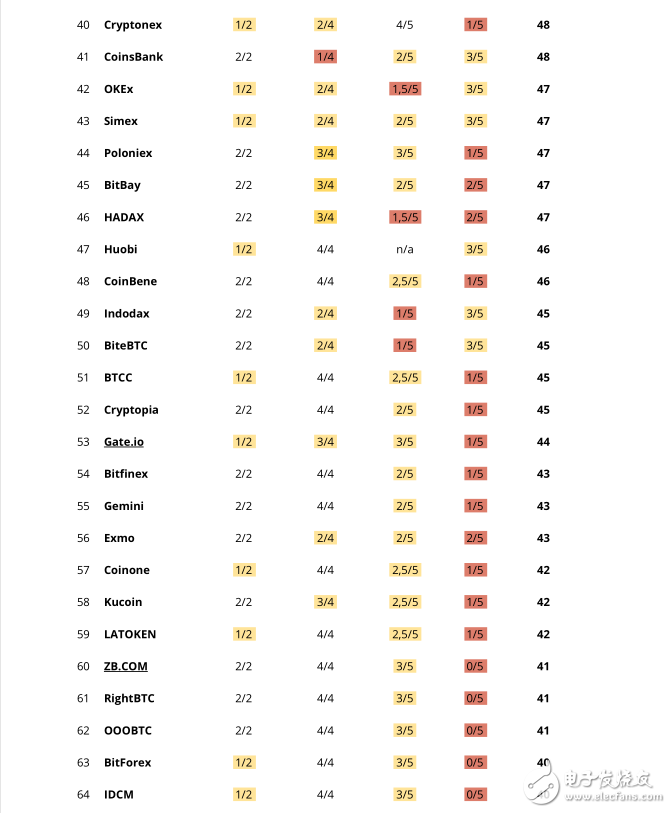
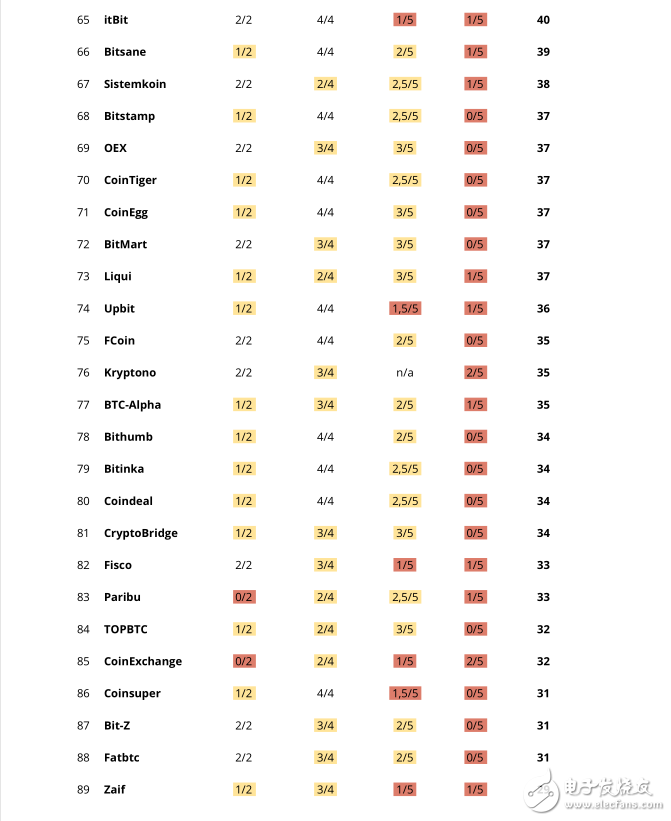
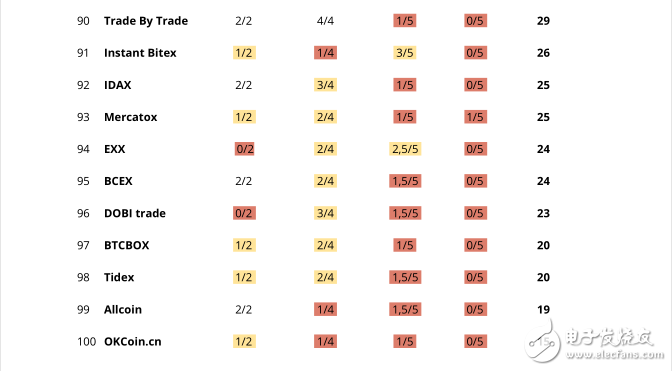
We select exchanges with a daily trading volume of more than $1 million; all of the 100 transactions on the list.
Console error
These errors in the code may cause some systems to malfunction, which can lead to system crashes and problems for users. However, this type of vulnerabilities is usually not important, and what needs to be considered is the losses that these vulnerabilities bring to users.
• Exchanges that have neither security measures nor warning users against such vulnerabilities: 49%
• No loopholes in the exchange: 68%
Conclusion: 32% of the exchanges have code errors, which will cause some operational defects for users.
User account security
A separate account has been created on each exchange. The following parameters are evaluated:
1. Possibility to create a password with less than 8 symbols
2. The possibility of using numbers or letters alone to create a password
3. Email verification immediately after account creation
4. The existence of 2FA
The evaluation results are as follows:
• 41% of exchanges allow passwords with less than 8 symbols
• 37% of exchanges allow the use of numeric or letter passwords
• 5% of exchanges allow account creation without email verification
• 3% of exchanges lack 2FA
• Only 46% of exchanges meet all four parameters
Registrar and domain security
We used the cloudflare platform (?https://?) to check whether these exchanges have vulnerabilities related to their registrars and domain names:
1. Registry lock? ; Registry lock is a special flag in the registry (not the registry), which prevents anyone from making changes to your domain without out-of-band communication with the registry.
2. Registrar lock; Registrar lock (not to be confused with registry lock) can prevent this from happening by requiring changes to the auth code instead of just requiring the domain name to hijack the global registry information.
3. Role accounts; security-conscious organizations avoid divulging the information of privately using role accounts to register their domain names. Role accounts protect individuals in the organization from being targeted by attackers.
4. Term; we recommend at least 6 months of validity. This leaves enough leeway to deal with unforeseen complex issues, such as employees who own the domain name leaving the company (again, this is a good reason to use role accounts).
5. DNSSEC; DNSSEC eliminates the threat of DNS cache poisoning by verifying all DNS queries with encrypted signatures. The DNS server will reject unauthenticated responses instead of blindly caching DNS records.
There are three possible outcomes for each item: all the items above are running correctly (1), no normal operation (0), and warning (0.5). The evaluation results are as follows:
• Only 2% of exchanges use registry locks
• Only 10% of exchanges use DNSSEC
• No transaction, all five questions are involved
• Only 4% of exchanges use 4 of these 5 fields
Web protocol security
We have checked whether the exchanges under review have headers that can ensure protection against various attacks. We used the following resource: https:// According to whether the exchange has the protocol, its score is 1 or 0. We checked the following headers
as follows:
1. Strictly transmit secure headers (http-Strictly Transmitted Security (HSTS) headers force browsers to browse websites with HTTPS).
2. x-xss protection header (x-xss protection defines how the browser should perform cross-site scripting protection)
3. The content security policy header (Content-Security-Policy, CSP) supports the definition of permitted sources for each type of content to help defend against XSS attacks.
It also allows to define some browser behaviors, such as sandbox enforcement, to send the value in the HTTP referrer header.
4. X-frame-options header (The X-frame-opTIons header specifies whether the website should allow itself to be framed, and from which origin. Blocking frames helps defend against attacks such as clickjacking.)
5. X-content-type-opTIons header (X-content-type-opTIons can guide the browser to disable the function of sniffing the content type of the page, and only use the content type defined in the instruction itself. This provides the XSS or drive-through Download protection attack.)
The evaluation results are as follows:
• Only 10% of exchanges have all five headers
• 29% of exchanges do not have the above header
• Only 17 exchanges have content security policy headers
General exchange security score
According to the above categories, the selected exchanges use the following scoring system:
• Console error: up to 5 points for each category, analysis of 2 parameters
• User account security: up to 18 points, analysis of 4 parameters
• Registrar and domain name security: up to 34 points, analysis of 5 parameters
• Web protocol security: up to 43 points, analysis of 5 parameters
The maximum score above is 100 points in total

Incremental encoders provide speed, direction and relative position feedback by generating a stream of binary pulses proportional to the rotation of a motor or driven shaft. Lander offers both optical and magnetic incremental encoders in 4 mounting options: shafted with coupling, hollow-shaft, hub-shaft or bearingless. Single channel incremental encoders can measure speed which dual channel or quadrature encoders (AB) can interpret direction based on the phase relationship between the 2 channels. Indexed quadrature encoders (ABZ) are also available for homing location are startup.
Incremental Encoder,6Mm Solid Shaft Encoder,Hollow Rotary Encoder,Elevator Door Encoder
Jilin Lander Intelligent Technology Co., Ltd , https://www.jllandertech.com