A protocol is a set of conventions that both parties to a computer must communicate with each other. TCP/IP (Transmission Control Protocol/Internet Protocol) is an agreement that dictates how computers communicate with each other. TCP/IP is a pre-defined set of formats and conventions that everyone can follow to enable normal data communication between heterogeneous networks and different devices connected to the Internet. The agreement was developed by the US Department of Defense's Advanced Research Projects Agency for the resume ARPANET. In this set of agreements, the two most well-known protocols are the Transmission Control Protocol (TCP) and the Internet Protocol (IP). The protocol set is called TCP/IP. The reason why TCP / IP is a protocol cluster is because TCP / IP includes TCP, IP, UDP, ICMP, RIP, TELNET, FTP, SMTP, ARP and many other protocols, addressing the host in the Internet, host The naming mechanism, the rules for the transmission of information, and various service functions have been elaborated. These conventions are collectively referred to as TCP/IP.
The TCP/IP protocol, like the Open Systems Interconnection Reference Model, is a hierarchical structure. The layering of the protocol makes the tasks and objectives of each layer very clear, which is beneficial to software writing and communication control. The TCP/IP protocol is divided into four layers, from bottom to top, the network interface layer, the internet layer, the transport layer, and the application layer, as shown in Figure 1-1.
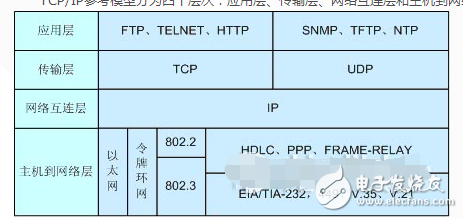
Figure 1-1 TCP/IP protocol hierarchy
1.2 Main features of the TCP/IP protocol
(1) Open protocol standards that can be used free of charge and are independent of specific computer hardware and operating systems;
(2) Independent of specific network hardware, it can run on LAN, WAN, and more suitable for the Internet;
(3) A unified network address allocation scheme, so that the entire TCP/IP device has a unique address in the network;
(4) Standardized high-level protocols that provide a variety of reliable user services.
1.3 Overview of the TCP/IP Protocol
Currently used on the Internet is the TCP/IP protocol. The TCP/IP protocol is called Transmission Control/Internet Protocol, which is the foundation of the Internet International Internet. TCP/IP is the basic communication protocol used in the network. The IP (Internet Protocol) full name is "Internet Interconnection Protocol", which is a protocol designed to communicate with each other for computer networks. TCP (Transfer Control Protocol) is a transmission control protocol. The TCP/IP protocol is a set of rules that enable all computer networks connected to the network to communicate with each other. It is precisely because of the TCP/IP protocol that the Internet has rapidly developed into the world's largest open computer communication network.
From the surface name, TCP/IP includes two protocols, Transmission Control Protocol (TCP) and Internet Protocol (IP). In fact, TCP/IP is actually a collection of protocols, which includes hundreds of various functions. protocol. Such as: remote login, file transfer and e-mail, etc., and TCP protocol and IP protocol are two basic important protocols to ensure the complete transmission of data. The reason why the IP protocol can interconnect various networks is because it converts various "frames" into an "IP datagram" format. This conversion is one of the most important features of the Internet. Therefore, the IP protocol enables various computer networks to communicate on the Internet, which is characterized by "openness." The basic transmission unit of the TCP/IP protocol is a datagram. The TCP protocol is responsible for dividing the data into several data packets, and adding a packet header to each data packet. The packet header has a corresponding number to ensure that the data can be restored to the original format at the data receiving end. The IP protocol is on each packet header. Also add the host address of the receiving end, so that the data determines the flow of data through the MAC address in the router. If data loss occurs during data transmission, data is distorted, etc., the TCP protocol automatically requests data retransmission and regroups. . In short, the IP protocol guarantees the transmission of data, while the TCP protocol guarantees the quality of data transmission. The transmission of TCP/IP protocol data is based on the 4-layer structure of the TCP/IP protocol: application layer, transport layer, network layer, and interface layer.
Security vulnerabilities at each protocol layer2.1 Security holes in the link layer
We know that in Ethernet, the channel is shared, and every Ethernet frame sent by any host will reach the Ethernet interface of all other hosts on the same network segment as the host. Generally, the CSMA/CD protocol makes the Ethernet When the network interface detects that the data frame does not belong to itself, it ignores it and does not send it to the upper layer protocol (such as ARP, RARP layer or IP layer). If we set or modify it slightly, we can make an Ethernet interface receive data frames that do not belong to it. For example, some implementations may use a faulty joint, a machine node that can receive all data frames. The countermeasures to address this vulnerability are: network segmentation, utilization of switches, dynamic hubs, and bridges to restrict and encrypt data streams (using one-time password technology) and disable miscellaneous contacts.
2.2 Network Layer Vulnerabilities
Almost all TCP/IP-based machines respond to ICMP echo requests. So if a hostile host runs multiple ping commands simultaneously to send a server an ICMP echo request that exceeds its processing power, it can flood the server to reject other services. In addition, the ping command can establish a secret channel in the allowed network so that the backdoor can be opened in the attacked system for convenient attacks, such as collecting information on the target and performing secret communication. The solution to the vulnerability is to reject all ICMP echo responses on the network.
2.3 IP Vulnerabilities
Once the IP packet is sent out of the network, the source IP address is almost unused, and is used only after the intermediate router drops it for some reason or reaches the target. This allows a host to send IP packets using the IP address of another host, as long as it can put such IP packets on the network. Therefore, if an attacker masquerades his host as a friendly host trusted by the target host, the source IP address in the sent IP packet is changed to the IP address of the trusted friendly host, and the trust relationship between the hosts is utilized (Unix network software). The terminology invented by the developer) and the vulnerability in the actual authentication of this trust relationship (identified only by IP) can attack the trusted host. Note that the trust relationship mentioned here means that an authorized host can conveniently access the trusted host. All r* commands use the trusted host scheme, so an attacking host can change its own IP to the IP of the trusted host, and can connect to the trusted host and use the r* command to open the backdoor to achieve the purpose of attack. One way to solve this problem is to have the router refuse to accept the entry of an IP packet from the IP address outside the network that is the same as the IP address of a local host.
2.4 ARP spoofing
The ARP protocol uses the ARP cache (also called the ARP table) when parsing the IP address. Each entry in the ARP cache holds a mapping of IP addresses to physical addresses. If there is no such corresponding entry in the ARP table, the ARP protocol broadcasts the ARP request, obtains the physical address corresponding to that IP address, and adds the correspondence to the ARP table. Each entry in the ARP table has a timer that is invalidated if the timer expires and is therefore removed from the cache. Obviously, if an attacker temporarily uses the IP address of a host that is not working, it can forge an IP-physical address correspondence pair and disguise itself as a host that is not used temporarily. The way to overcome this problem is to have the hardware address resident in memory and manually join it with ARP commands (privileged users can do that); you can also check the client's ARP spoofing by asking the RARP server. Because the RARP server retains information about the hardware address and IP in the network.
2.5 route spoofing
In a routing protocol, a host uses a redirect message to change or optimize a route. If a router sends an illegal redirect message, it can forge the routing table and incorrectly direct non-local datagrams. In addition, each router periodically broadcasts routing information to its neighboring routers. If the 520 port of the host using RIP privilege broadcasts illegal routing information, the route spoofing can also be achieved. To solve these problems, you can prevent route spoofing by setting the host to ignore the redirect information; prohibit the router from passively using RIP and restricting the scope of passive use of RIP.
2.6 DNS spoofing
All hosts on the network trust the DNS server. If the data in the DNS server is destroyed by an attacker, DNS spoofing can be performed.
2.7 Intercepting TCP connections
The attacker can make both ends of the TCP connection enter an unsynchronized state, and the intruder host sends the forged data packet to both ends. Pretending to be a trusted host to establish a TCP connection, flooding the trusted host with SYN, and guessing the response in the 3-step handshake (establishing multiple TCP connections to the trusted host, obtaining the initial serial number ISN (IniTIal Serial Number) and RTT, then Guess the response ISN because the serial number adds 64000 every half second, plus 64000 for each connection. Prevention: Disable all r* commands and let the router reject packets from the outside with the same IP address as the local host. RARP queries can be used to discover attacks from hosts on the same physical network as the target server. In addition, ISN attacks can be prevented by having each connected ISN randomly assigned to add 64000 every half second.
2.8 Flooding the server with TCP/SYN segments
The shortcomings of the three steps of establishing a connection by using TCP and the limitation of the number of connections allowed by the server port, stealing the unreachable IP address as the source IP address, so that the server does not get the ACK and the connection is in a half-open state, thereby preventing the server from responding to the response. Connection request. Although the half-open connection will be closed and expired, as long as the attack system sends spoofed SYN requests faster than expired, the attack can be achieved. This method of attack has always been an important method of attacking an ISP (Internet Service Provider). This kind of attack does not damage the service, but weakens the service capability. The solution to this attack is to add a patch to the Unix kernel or use some tools to configure the kernel. It is common practice to increase the number of allowed half-open connections and to allow the connection to be in a half-open state for a shorter period of time. But these do not solve these problems fundamentally. In fact, there is a special queue in the system's memory that contains all the half-open connections. The size of this queue is limited, so if you intentionally make the server establish too many half-open connections, you can make this queue of the server overflow. Respond to other customers' connection requests.
Analysis of the vulnerability of the TCP/IP protocol family3.1 The TCP/IP protocol family is vulnerable
The main curve of the IP layer is the lack of effective security authentication and confidentiality mechanisms. The most important factor is the IP address problem. The TCP/IP protocol uses IP addresses as the unique identifier for network nodes. Many TCP/IP services, including R commands, NFS, and X Window in Berkeley, authenticate and authorize users based on IP addresses. The security mechanism of the current TCP/IP network is mainly based on packet filtering and authentication (AuthenTIcaTIon) technology of IP address, and its effectiveness is reflected in the authenticity and security of the data according to the source IP address in the IP packet. . However, there are many problems with IP addresses. The biggest disadvantage of the protocol is the lack of protection for IP addresses and the lack of authentication mechanisms and confidentiality measures for the authenticity of source IP addresses in IP packets. This is the root cause of the insecurity of the entire TCP/IP protocol.
Since UDP is based on the IP protocol, TCP segmentation and UDP protocol packets are encapsulated in IP packets and transmitted over the network, so they also face security threats encountered by the IP layer. Now people have been trying to solve the problem, but still can not avoid is based on the "three-way handshake" mechanism of the TCP connection establishment.
3.2 Application services are not optimistic
3.2.1 File Transfer Protocol
The reason why FTP is enduring is that it can perform platform-independent data transmission over the Internet, based on a client/server architecture. FTP will be transmitted over two channels (ports), one to transmit data (TCP port 20) and the other to transmit control information (TCP port 21). Above the control channel, both parties (client and server) exchange commands for initiating data transfers. An FTP connection consists of four steps: user authentication → establish control channel → establish data channel → close the connection. FTP connection control uses TCP (Transmission Control Protocol), which guarantees reliable transmission of data. Therefore, FTP does not need to care about packet loss and data error detection in data transmission.
Anonymous FTP is widely used as a service on the Internet, and the low level of security has been frequently visited by hackers. Anonymous FTP is really anonymous, and it does not record who requested what information, who downloaded the file, what was uploaded (probably a Trojan). FTP has a fatal security flaw. FTP uses a standard username and password for authentication. It lacks a valid access control mechanism, and its password and password are also transmitted in plain text.
3.2.2 Web Services
The web server is located at the front end of the hosting infrastructure. It is directly connected to the Internet and is responsible for receiving requests from clients, creating dynamic web pages and responding to request data. Initially, the WWW service only provided static HTML pages. In order to change people's desire for network interaction requests, CGI programs were introduced, and CGI programs made the homepage active. The CGI program can receive input information from the user. The general user passes the input information to the CGI program through the form, and then the CGI program can perform some processing according to the user's request. In general, an HTML file is generated and transmitted back to the user. Many CGI programs have security vulnerabilities that are easily exploited by hackers to do something illegal. Now many people are not familiar with the security vulnerabilities in CGI packages when writing CGI programs, and in most cases will not rewrite all parts of the program, just modify them appropriately, so many CGI programs can not Avoid the same security holes. Many SQL Server developers don't start with the security foundation at the beginning of the code, so you can't ensure the security of the code you develop. As a result, you can't control the running of the application to the minimum required. within.
3.3 Improve network credibility
The drawbacks of the previous IPv4, many security technologies have been ignored, it is inevitably replaced by the new generation of technology IPv6. The IPsec security protocol is a protocol developed afterwards (Figure 3-1), while NAT (Network Address TranslaTIon) solves the problem of IP address shortage, but increases security risks and makes true end-to-end security. The application is difficult to implement. The two basic components of end-to-end security—authentication and encryption—are integrated components of the IPv6 protocol; in IPv4, they are just add-ons, so IPv6 security is easier and more consistent.
In the current network environment, especially in the campus network, because there is no problem of NAT address translation, IPSec has the basic features that allow the deployment of trusted computing infrastructure. IPSec packet verification ensures data integrity throughout the IP header, next layer protocol (eg TCP, UPD or ICMP) headers and packet payload. Huaxia Network Management ofAdmin.Com
In addition, a one-way hash algorithm for the data packet is used to provide a checksum. The communication initiator calculates the checksum and appends it to the packet before sending it; the responder calculates a checksum for it after receiving the packet. If the checksum calculated by the responder exactly matches the checksum attached to the packet, it proves that the packet was not modified during transmission. The one-way calculation feature of the checksum means that its value cannot be modified during transmission, which ensures the credibility of the end-to-end data transmission process.
Babbitt wire is with tin as the base, the product is added with certain amount of antimony, copper
or other improved elements.
Sn Sb7Cu3 Babbit metal is suitable for metal spraying on the end face of metalized ï¬lm capacitor. With strong adhesive force, good weldability and low loss angle, it is an ideal metal spraying material for laminated capacitor.
Other trade marks are suitable to use CMT, TIG and MIG technology to manufacture sliding bearing bush material layer. It is of high bonding strength with substrate, with material utilization rate of 70~80%. It has small amount of ingredient segregation without any loose or slag inclusion. The internal control standard of the alloy composition is prevailing over GB/T8740-2013. Babbi1 metal added with improved elements can substantially enhance the service life.
Snsbcu Babbitt Wire,Overlaying Materials,Thermal Spray Babbitt Wire,Babbitt Wire
Shaoxing Tianlong Tin Materials Co.,Ltd. , https://www.tianlongspray.com